Meet Paragon Apartheid Israel Surveillance Startup Hacks WhatsApp Signal cofounding director known pedophile Ehud Barak
Publication date 2021-08-02
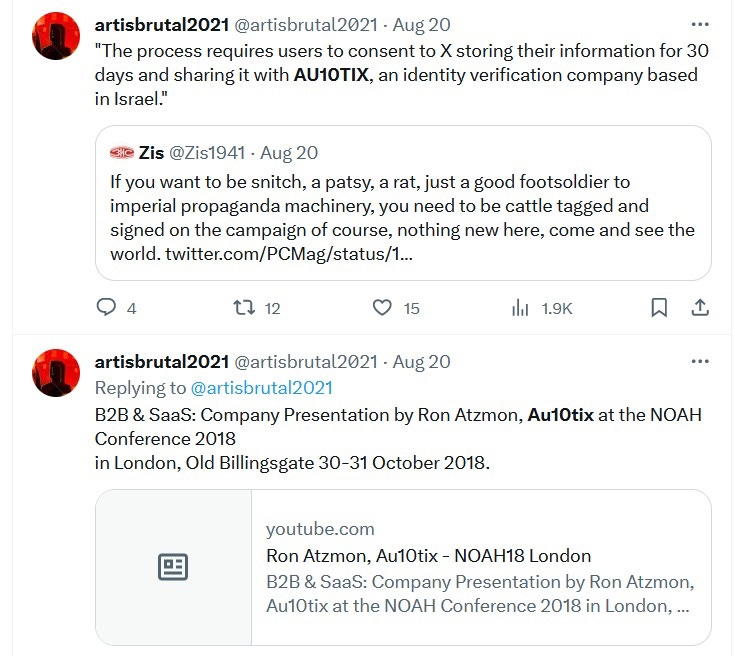
Meet Paragon: An American-Funded, Super-Secretive Israeli Surveillance Startup That ‘Hacks WhatsApp And Signal’
Paragon Solutions doesn’t have a website. There’s very little information at all about them online, even if the Tel Aviv-based smartphone
surveillance startup’s employees are all over LinkedIn, more than 50 of them.
But it does have a cofounder, director and chief shareholder that will turn heads: Ehud Schneorson, the former commander of Israel’s
NSA equivalent, known as Unit 8200. The other cofounders - CEO Idan Nurick, CTO Igor Bogudlov and vice president of research
Liad Avraham - are ex-Israeli intelligence too. Also on the board is cofounding director and former Israeli prime minister
Ehud Barak.
Paragon’s product will also likely get spyware critics and surveillance experts alike rubbernecking: It claims to give
police the power to remotely break into encrypted instant messaging communications, whether that’s WhatsApp, Signal,
Facebook Messenger or Gmail, the industry sources said. One other spyware industry executive
said it also promises to get longer-lasting access to a device, even when it’s rebooted.
https://www.forbes.com/sites/thomasbrewster/2021/07/29/paragon-is-an-nso-competitor-and-an-american-funded-israeli-surveillance-startup-that-hacks-encrypted-apps-like-whatsapp-and-signal
https://web.archive.org/web/20210802005010/https://www.forbes.com/sites/thomasbrewster/2021/07/29/paragon-is-an-nso-competitor-and-an-american-funded-israeli-surveillance-startup-that-hacks-encrypted-apps-like-whatsapp-and-signal/
Former ISRAELI PM named as SEX OFFENDER in Epstein court filings submitted by Dershowitz
https://www.rt.com/news/492823-epstein-defamation-dershowitz-barak-israel/
Usage Public Domain Mark 1.0
Topics
Paragon, Apartheid Israel, Ehud Barak Pedophile, Jeffrey Epstein, Surveillance startup, Hacking, WhattsApp
Meet Paragon: An American-Funded, Super-Secretive Israeli Surveillance Startup That ‘Hacks WhatsApp And Signal’
Forbes Staff.
Senior writer at Forbes covering cybercrime, privacy and surveillance.
Follow Author
Jul 29, 2021, 12:30pm EDTUpdated Jul 30, 2021, 06:58am EDT
Share
SaveComment0
But it does have a cofounder, director and chief shareholder that will turn heads: Ehud Schneorson, the former commander of Israel’s NSA equivalent, known as Unit 8200. The other cofounders - CEO Idan Nurick, CTO Igor Bogudlov and vice president of research Liad Avraham - are ex-Israeli intelligence too. Also on the board is cofounding director and former Israeli prime minister Ehud Barak. They also have a significant American financial backer: Boston, Massachusetts-based Battery Ventures. According to two senior employees at companies in the Israeli surveillance industry, who spoke on the condition of anonymity, the venture capital business put in between $5 and $10 million, though Battery declined to comment on the nature of its investment, which is only mentioned in brief on the company’s website.
Paragon’s product will also likely get spyware critics and surveillance experts alike rubbernecking: It claims to give police the power to remotely break into encrypted instant messaging communications, whether that’s WhatsApp, Signal, Facebook Messenger or Gmail, the industry sources said. One other spyware industry executive said it also promises to get longer-lasting access to a device, even when it’s rebooted.
The startup, founded in 2019, is quietly building up steam at a time when its ilk in the smartphone hackers-for-hire industry are under heavy fire. The Pegasus Project, a coalition of nonprofits and global publications, this month claimed to have uncloaked worldwide surveillance of journalists, lawyers and high-profile elected politicians by clients of Israel’s best known spyware provider NSO Group. The company’s CEO has rebuffed the claims made by the Project’s partners, saying it had no evidence that its tools were used to target those named in reports, from the wife of murdered journalist Jamal Khashoggi to French president Emmanuel Macron. The French government has already begun its investigation, but other administrations around the world are now being called on to probe just who was hacked by NSO’s spyware and why. Even before the Pegasus Project, Microsoft president Brad Smith warned the $12 billion industry as a whole represented a threat, writing: “An industry segment that aids offensive cyberattacks spells bad news on two fronts. First, it adds even more capability to the leading nation-state attackers, and second, it generates cyberattack proliferation to other governments that have the money but not the people to create their own weapons. In short, it adds another significant element to the cybersecurity threat landscape.”
A senior executive at Paragon, who declined to comment on the record, told Forbes that he did not want to talk about its products. He said the company does not yet have customers. But, in an attempt to avoid the trouble NSO has had with some of its clients who were barred over misuse, the executive added that Paragon would only sell to countries that abide by international norms and respect fundamental rights and freedoms. Authoritarian or non-democratic regimes would never be customers, he added.
Two industry sources said they believed Paragon was trying to set itself apart further by promising to get access to the instant messaging applications on a device, rather than taking complete control of everything on a phone. One of the sources said they understood that Paragon’s spyware exploits the protocols of end-to-end encrypted apps, meaning it would hack into messages via vulnerabilities in the core ways in which the software operates.
The company’s staff, according to LinkedIn profiles, have strong backgrounds in surveillance, with its VP of operations and HR lead being ex-NSO, and many of its developers coming from Israel Defense Forces intelligence units. One of its software developers, Alon Weinberg, previously presented research on hacking the software running on Intel and AMD chips at famous U.S. hacking conference Def Con.
Israeli surveillance on American money
With an American backer, it appears Paragon is going to try and crack American law enforcement agencies where others like NSO have failed. According to a LinkedIn profile, a 30-year veteran of Israeli intelligence, Menachem Pakman, has been employed to help find business in the U.S. There’s no indication that they have clients across the Atlantic yet, however.
According to the corporate filing for the company, Battery invested via two of its venture capital vehicles in September 2019, indicating it helped launch the business, while its Israel-based vice president Aaron Rinberg is a board observer at Paragon. Battery, which has raised more than $9 billion since its founding in 1983, has claimed some hugely successful investments in its time, including Coinbase, Groupon, Splunk, SkullCandy and Pokémon Go creator Niantic. The company hadn’t commented on its investment in the Israeli smartphone surveillance game at the time of publication.
John Scott-Railton, senior researcher at Citizen Lab at the University of Toronto’s Munk School, said that if the aim of Paragon’s business is to help American agencies target Americans, then it needs to be scrutinized. “Any American investor that is putting money into the industry right now, urgently needs serious scrutiny. We are going to need to know who their customers are. We’ve learned what happens when the industry operates in secrecy and says they care about protecting human rights,” he said. “The hack-for-hire industry has gone way far out on a legal limb.” The Paragon executive said the company would not disclose future customers.
Paragon isn’t the first Israeli company to take American venture capital on launch. Toka, which focuses on helping law enforcement hack into Internet of Things devices like Amazon Echos for forensics or during property raids, raised $12.5 million in 2018, in a round that included funding from Dell Technologies Capital and Andreessen Horowitz. NSO, meanwhile, was majority-owned by U.S. private equity firm Francisco Partners until a U.K. private equity company, Novalpina Capital, took control.
Paragon’s leadership are also in the interesting position of working for both cyber defense and offensive companies. In 2019, the same year they set up Paragon, Nurick and Schneorson unveiled a company they had cofounded, Hunters.ai, a startup promising artificial intelligence that can hunt down hackers on a network and is backed by Microsoft’s investment arm M12. (After publication, a current investor in Hunters.ai told Forbes both departed the company early on and have no shares or involvement in the business.) Schneorson was also named as an advisor for ZecOps, a mobile security business that has, in the past, uncovered phone hacks developed by surveillance businesses. (ZecOps CEO Zuk Avraham hadn’t responded to a request for comment at the time of publication.)
Virtue or Vice? A First Look at Paragon’s Proliferating Spyware Operations
By Bill Marczak, John Scott-Railton, Kate Robertson, Astrid Perry, Rebekah Brown, Bahr Abdul Razzak, Siena Anstis, and Ron Deibert
March 19, 2025
Clicca qui per leggere un riassunto del report in italiano.
Key Findings
Introducing Paragon Solutions. Paragon Solutions was founded in Israel in 2019 and sells spyware called Graphite. The company differentiates itself by claiming it has safeguards to prevent the kinds of spyware abuses that NSO Group and other vendors are notorious for.
Infrastructure Analysis of Paragon Spyware. Based on a tip from a collaborator, we mapped out server infrastructure that we attribute to Paragon’s Graphite spyware tool. We identified a subset of suspected Paragon deployments, including in Australia, Canada, Cyprus, Denmark, Israel, and Singapore.
Identifying a Possible Canadian Paragon Customer. Our investigation surfaced potential links between Paragon Solutions and the Canadian Ontario Provincial Police, and found evidence of a growing ecosystem of spyware capability among Ontario-based police services.
Helping WhatsApp Catch a Zero-Click. We shared our analysis of Paragon’s infrastructure with Meta, who told us that the details were pivotal to their ongoing investigation into Paragon. WhatsApp discovered and mitigated an active Paragon zero-click exploit, and later notified over 90 individuals who it believed were targeted, including civil society members in Italy.
Android Forensic Analysis: Italian Cluster. We forensically analyzed multiple Android phones belonging to Paragon targets in Italy (an acknowledged Paragon user) who were notified by WhatsApp. We found clear indications that spyware had been loaded into WhatsApp, as well as other apps on their devices.
A Related Case of iPhone Spyware in Italy. We analyzed the iPhone of an individual who worked closely with confirmed Android Paragon targets. This person received an Apple threat notification in November 2024, but no WhatsApp notification. Our analysis showed an attempt to infect the device with novel spyware in June 2024. We shared details with Apple, who confirmed they had patched the attack in iOS 18.
Other Surveillance Tech Deployed Against The Same Italian Cluster. We also note 2024 warnings sent by Meta to several individuals in the same organizational cluster, including a Paragon victim, suggesting the need for further scrutiny into other surveillance technology deployed against these individuals.
1. Background: Paragon Solutions
This section provides a brief background on Paragon’s corporate structure.
Paragon Solutions Ltd.
Paragon Solutions Ltd. was established in Israel in 2019. The founders of Paragon include Ehud Barak, the former Israeli Prime Minister, and Ehud Schneorson, the former commander of Israel’s Unit 8200. Paragon sells a spyware product called Graphite, which reportedly provides “access to the instant messaging applications on a device, rather than taking complete control of everything on a phone,” like NSO Group’s Pegasus spyware.
According to a Forbes report from 2021, a senior executive at Paragon said the company would only sell to government customers who “abide by international norms and respect fundamental rights and freedoms” and that “authoritarian or non-democratic regimes would never be customers.”
Paragon Solutions (US) Inc.
Paragon Solutions (US) Inc. was established as a Delaware corporation in March 2021. In October 2022, Paragon US obtained a certificate to conduct business in Virginia.
Paragon US’s senior leadership is composed of American personnel with links to the US government, including a CIA veteran, a former service member and Navy program director that also worked at Twitter, and a former director of contracts at the defense contractor L3Harris.
Paragon Parent Inc.
According to corporate records, on December 13, 2024, all shares in Paragon Israel were transferred to a US company, Paragon Parent Inc. This deal was reportedly worth $500 million upfront, with an additional $400 million payable if Paragon Israel reached set performance targets.
Paragon Parent Inc. was registered in Delaware on October 7, 2024. Shareholder information for Paragon Parent is not publicly available, though reporting suggests that US private equity firm AE Industrial Partners (AEI) acquired Paragon Israel with the intention of merging it with US cybersecurity company, REDLattice Inc.
The reported merger further bolsters Paragon’s high-ranking intelligence and military connections. According to recent SEC filings, board members of the REDLattice company, REDL Ultimate Holdings (a company linked to RedLattice according to corporate records), include Andrew Boyd, a former senior executive at the CIA and US Air Force, and James McConville, the former Chief of Staff of the US Army.
Paragon’s US Business
While the specific nature of the relationship between Paragon Solutions (US) Ltd. and Paragon Parent Inc. are hard to discern, the presence of Paragon Solutions in the US marketplace is noteworthy. In 2022, the New York Times reported that the Drug Enforcement Administration (DEA) had used Paragon’s Graphite spyware. On the other hand, recent contracting between Immigration and Customs Enforcement (ICE) and Paragon Solutions was reportedly paused under White House review at the end of 2024. Notably, at least 36 civil society organizations expressed concern and called for transparency after this contract was first reported by Wired. The status of that contract is currently unknown.
2. Mapping Paragon’s Infrastructure
Our initial investigation into Paragon began with mapping infrastructure that we believe Paragon and its government customers use to carry out or support spyware attacks. We find that this infrastructure included cloud-based servers likely rented by Paragon and/or its customers, as well as servers likely hosted on the premises of Paragon and its government customers.
Tier 1: Victim-Facing Servers
In 2024, we received a tip from a collaborator about a single piece of infrastructure: a domain name pointing to a server that also returned several distinctive self-signed TLS certificates. The certificates had multiple curious elements, including various pieces of missing information and a distinctive naming scheme. We developed Fingerprint P1 for these certificates:
Fingerprint P1:
parsed.validity_period.length_seconds=31536000 and
parsed.extensions.subject_alt_name.dns_names=/.+/ and not
parsed.extensions.subject_alt_name.uniform_resource_identifiers=/.+/ and not
parsed.extensions.key_usage.value=[0 to 255] and not
parsed.extensions.extended_key_usage.server_auth=`true` and
parsed.subject_dn=/O=[a-z0-9\-\.]+, CN=[a-z0-9\-\.]+/ and
(parsed.issuer_dn=/O=[a-z0-9\-\.]+, CN=[a-z0-9\-\.]+/ or not
parsed.issuer_dn=/.+/) and ((parsed.extensions.subject_key_id=/.+/ and parsed.extensions.authority_key_id=/.+/) or
(not parsed.extensions.subject_key_id=/.+/ and not parsed.extensions.authority_key_id=/.+/)) and not
parsed.extensions.basic_constraints.is_ca=true and not
parsed.extensions.basic_constraints.is_ca=false and labels=`unexpired`
Using this fingerprint, we found 150 related certificateson Censys
with approximately half of the certificates actively served on IP addresses. The IP addresses appear to be primarily sourced from cloud-based server rental companies. The infrastructure appears to be consistent with a dedicated command and control infrastructure (“Tier 1”). We would expect victim devices to communicate with this infrastructure under certain conditions.
Pivoting to Tier 2: Paragon and Customer Endpoints
While conducting our investigation, we observed two Tier 1 IPs (matching Fingerprint P1) that also returned a different type of certificate:
The first IP, 84.110.122[.]27, appears to be a static IP address geolocated to Israel. The IP address returned the forti.external-Staging-02[.]com certificate until January 2024. Between July 2023 and September 2023, it returned both the aforementioned forti.external-Staging-02[.]com certificate as well as several Tier 1certificates. We developed the P2 fingerprint for this certificate:
Fingerprint P2:
parsed.issuer.organization=”Internet Widgits Pty Ltd” and
parsed.extensions.subject_alt_name.dns_names=/.+/ and
parsed.extensions.key_usage.value=96
When we checked, Censys recorded 47 certificates
matching Fingerprint P2. The results included a certificate with the exact same subject and issuer DN as the certificate returned by the second IP, 178.237.39[.]204. However, the certificate returned by 178.237.39[.]204 had a different hash. We further noted that in fact, all 47certificates matching Fingerprint P2 had a “twin” certificate not matching Fingerprint P2, but with identical issuer DN, and either identical subject DN, or a subject DN identical except with the addition of a subdomain “forti” to the common name. We define certificates matching Fingerprint P2, as well as their twins, to be Tier 2 certificates.
The IPs that returned these certificates were often notcloud-based servers (as with Tier 1 infrastructure), but were instead IPs procured from local wireline telecommunications operators. Thus, we suspected that they might be run directly from Paragon and customer premises.
Tier 2 Nodes in Israel Have Links to “Paragon”
Examining Censys records shows that at various times, a range of static IPs in Israel (84.110.47.82 – 84.110.47.86) returned Tier 2 certificates:
IPs in the same range also returned self-signed certificates matching Fingerprint P3:
Fingerprint P3:
parsed.issuer_dn=”C=US, ST=CA, CN=Root CA”
Censys’ Certificates dataset records a total of eight certificates matching Fingerprint P3 (though the Hosts dataset records additional ones that are missing from the Certificates dataset, perhaps due to Censys data loss around this time).
In all cases we identified, after the “dashboard” certificate was returned, a page with the title “Paragon” was returned:
A Link to “Graphite”
We looked for related certificates with the same “installerserver” name using Fingerprint P4:
Fingerprint P4:
parsed.subject.common_name=”installerserver” and
parsed.issuer.common_name=”Root CA”
This yielded only one certificate not included in the results of Fingerprint P3: a certificate apparently created in November 2019 with the organization name “Graphite”.
It is not clear which IP address returned this certificate, as historical Censys data for that time period appears to be incomplete.
Attribution of Infrastructure to Paragon
In summary, strong circumstantial evidence supports a link between Paragon and the infrastructure we mapped out. The infrastructure we found is linked to webpages entitled “Paragon” returned by IP addresses in Israel (where Paragon is based), as well as a TLS certificate containing the organization name “Graphite”, which is the name of Paragon’s spyware, and the common name “installerserver” (Pegasus, a competitor spyware product, uses the term “Installation Server” to refer to a server designed to infect a device with spyware).
Tier 2 Nodes Highlight Several Potential Paragon Customers
We identified other interesting IPs apparently procured from local telecom companies that returned Tier 2certificates. Because the IPs appear to belong to local telecom companies rather than cloud-based server rental companies, we suspect these IPs belong to Paragon’s customer deployments. We also note that the first letter of each customer’s apparent “codename” matches the first letter of the country associated with the customer’s IP address (except in the case of Israel).
In addition, we noted that Tier 2 certificates were returned by at least eleven IPs that geolocate to a German datacenter of Digital Realty, a datacenter holding company. The IPs were all registered to a single “Digital Realty DE IP Customer” ID, and certificates returned included various codenames, like “nelly”, “soundgarden”, “slash”, “galaxy”, and “chance”. Additionally, the use of names such as “p-internal”, “p-external”, and “access” and “management” leads us to believe that Digital Realty’s customer may be Paragon. More recently, Paragon deployments appear to use more ambiguous codenames in the form of fictitious domains such as “anxious-poet” or “sincere-cookie”.
Note that this methodology cannot enumerate all customers, as no Internet scanning service (e.g., Censys) has a complete historical view of the Internet at all times. Furthermore, some customers likely took measures to prevent their infrastructure from being exposed in Internet scans. For example, Italy is an admitted Paragon customer (see: Section 4).
“Cap”: Registration Information Raises Canadian Questions
The IP address for the Canadian customer Cap was delegated to ARIN customer C06874702, named “Integrated Communications.” We searched ARIN’s WHOIS data and found five additional “Integrated Communications” customers in Canada, all in Ontario (C02423261, C07940612, C09095096, C10862989, C10948330). Each customer controls a single range of 8 or 16 IP addresses.
The address of one of the customers, C10862989, matches that of the “Ontario Provincial Police – General Headquarters.” The other customer addresses include what appear to be a shared warehouse, a strip mall, a brewery, and an apartment. The small number of customers named “Integrated Communications”, the fact that all such customers in Canada are in Ontario, and the use of the Ontario Provincial Police (OPP) address for one of them, suggests the OPP as a potential Paragon Solutions customer.
Canadian Law Enforcement’s History with Surveillance
The OPP has previously been linked to other instances involving the procurement or use of controversialsurveillance technologies. In 2019, the Toronto Starreported that for several years the OPP was the only police service in Canada to procure cell site simulator technology (i.e., “Stingray” equipment) which can be used to intercept private communications. In 2020, The Citizen Lab reported that the OPP developed and deployed technology to scrape communications from private, password-protected online chatrooms without obtaining judicial authorization for the mass interceptions.
In 2022, the Royal Canadian Mounted Police (RCMP), Canada’s national police force, disclosed that the RCMP had been using spyware from an unnamed vendor. The RCMP referred to the spyware as an “On-Device Investigative Tool” (ODIT)
, and said it had used ODITs in 32 investigations between 2017 and 2022. The RCMP did not consult with the public, or the Privacy Commissioner of Canada on its use of ODITs. Canada’s Public Safety Minister refused to disclose which vendors supplied RCMP with ODITs, and did not deny that other government agencies might also use ODITs.
Public records obtained and reviewed by The Citizen Lab suggest there is a growing ecosystem of spyware capability among Ontario-based police services. According to public court records obtained by The Citizen Lab, the OPP used the RCMP’s ODITs in the course of a 2019 investigation to infect a mobile phone for remote interception of private communications. A 2023 judgment from the Superior Court of Justice in Toronto describes a joint investigation between the Toronto Police Service and the York Regional Police Service where investigators had considered the use of an ODIT. The Citizen Lab also obtained an additional public court record (a 2023 search warrant application) prepared by the Toronto Police Service (TPS), which reveals that the TPS has independently obtained ODIT software from an unknown source. The application sought authorization to use ODIT software to remotely intercept cellular communications sent through encrypted instant messaging applications.
In the course of the preparation of this report, we have also learned through informal consultations of other cases that have been–or currently are–before the courts in Ontario involving other police services that now also possess or have sought authorization to deploy ODITs, including the OPP, York Regional Police Service, Hamilton Police Service, and Peel Regional Police Service. The apparent expansion of spyware capabilities to potentially multiple police services across Ontario reflects a widening gap in public awareness surrounding the extent to which mercenary spyware is being deployed in Canada.
3. WhatsApp’s Paragon Investigation
We shared details about our mapping of Paragon’s infrastructure (Section 2) with Meta, because we believed that WhatsApp might be used as an infection vector. Meta told us that these details were pivotal to their ongoing investigation into Paragon. Meta shared information with WhatsApp that led them to identify, mitigate, and attribute a Paragon zero-click exploit. On January 31, 2025, WhatsApp sent notifications to approximately 90 WhatsApp accounts they believed were targeted with Paragon’s spyware, including journalists and members of civil society.
The Citizen Lab coordinated with WhatsApp to ensure that targets in civil society were offered additional support and optional forensic analysis. In Italy, several individuals that chose to participate in forensic analysis with the Citizen Lab spoke out publicly about receiving notifications from WhatsApp (Section 4). They include a journalist and multiple members of civil society that work in organizations involved in the rescue of refugees and migrants at sea.
4. Paragon Targets: The Italian Connection
This section describes our forensic analysis of the devices of targets who received Paragon notifications from WhatsApp, as well as our analysis of a potentially related iPhone case.
Multiple WhatsApp notification recipients in Italy elected to participate in The Citizen Lab’s research program and have The Citizen Lab forensically analyze their devices. They are identified below, with their consent:
Francesco Cancellato is the Editor in Chief of Fanpage.it, an Italian online news outlet known for investigative journalism and reporting on political topics. The outlet has reported on connectionsbetween extremist elements and Italian Prime Minister Meloni’s party.
Luca Casarini is the founder of Mediterranea Saving Humans, an organization known for rescuing migrants from the Mediterranean Sea. Mr. Casarini is well-known for his criticism of the Meloni government’s treatment of migrants. Mr. Casarini is also a personal friend of Pope Francis.
Dr. Giuseppe “Beppe” Caccia is an Italian scholar and co-founder of Mediterranea Saving Humans. Dr. Caccia works closely with Mr. Casarini.
Forensically Confirming Android Paragon Infections
In the course of our investigation into Paragon we obtained BIGPRETZEL, an Android forensic artifact that we believe uniquely identifies infections with Paragon’s Graphite spyware. We analyzed the Android devices of the three individuals identified above. Based on their receipt of the WhatsApp notification, we believe all were targeted with Paragon spyware. We found traces of BIGPRETZEL on two devices. WhatsApp has also confirmed to The Citizen Lab that they believe that BIGPRETZEL is attributable to a Paragon spyware infection, and provided us with the following statement:
WhatsApp’s Statement: We can confirm that we believe that the indicator Citizen Lab refers to as BIGPRETZEL is associated with Paragon. We’ve seen first-hand how commercial spyware can be weaponized to target journalists and civil society, and these companies must be held accountable. Our security team is constantly working to stay ahead of threats, and we will continue working to protect peoples’ ability to communicate privately.
Given the sporadic nature of Android logs, the absence of a finding of BIGPRETZEL on a particular device does not mean that the phone wasn’t successfully hacked, simply that relevant logs may not have been captured or may have been overwritten. We also believe that the forensic indicators we have surfaced during this analysis may not fully capture the complete retrospective timeframe of infections for the same reasons. There may have been infections prior to the period observed, but not captured in the logs. Our forensic analysis is ongoing.
Dr. Caccia’s phone showed traces of BIGPRETZEL at several times, indicating that Paragon’s spyware was running on or around these times:
2024-12-22 – BIGPRETZEL present.
2024-12-26 – BIGPRETZEL present.
2025-01-03 – BIGPRETZEL present.
2025-01-13 – BIGPRETZEL present.
2025-01-23 – BIGPRETZEL present.
2025-01-28 – BIGPRETZEL present.
2025-01-31 – BIGPRETZEL present.
Additionally, analysis of Dr. Caccia’s phone showed evidence that the spyware had also infected two other apps on the device, including a popular messaging app. We have shared forensic indicators with the developers of that app, who confirm that their investigation is ongoing.
Mr. Casarini’s phone showed traces of BIGPRETZEL on at least one date:
2024-12-23 – BIGPRETZEL present.
Given limited available indicators, we were unable to determine if the spyware had loaded itself into other apps on Mr. Casarini’s device, but cannot exclude the possibility.
A Related iPhone Spyware Victim: Is it Paragon?
On November 13, 2024 (approximately two-and-a-half months before the WhatsApp notifications), David Yambio–a close associate of Mr. Casarini and Dr. Caccia–was notified by Apple that his iPhone had been targeted with mercenary spyware.
Mr. Yambio is an Italy-based founder of the organization Refugees in Libya. Mr. Yambio’s work focuses on advocating for lifesaving efforts for migrants that cross the Mediterranean, and on helping victims seek justice and accountability for abuses committed in Libya. He is a former child soldier kidnapped by the Lord’s Resistance Army who eventually escaped and was able to reach Europe where he claimed asylum. During this journey, he was tortured while in detention in Libya.
After he received the Apple notification, Mr. Yambio contacted digital security expert Artur Papyan of Cyber HUB-AM for assistance. Mr. Papyan performed an initial screening of the device supported by The Citizen Lab which identified potential anomalies. We immediately began an investigation into Mr. Yambio’s case, and Mr. Papyan provided extensive support in collecting forensic artifacts from the device.
While our investigation was ongoing, multiple close associates of Mr. Yambio also received notifications from WhatsApp concerning Paragon targeting of their Android devices, including Mr. Casarini and Dr. Caccia.
Analysis of Mr. Yambio’s Device
We found that Mr. Yambio’s device showed clear signs of implausible CloudKit activity relating to the appleaccountd process on 13 June 2024. We call this activity SMALLPRETZEL. The device did not test positive for any indicators we link to other spyware types, including NSO Group’s Pegasus, Intellexa’s Predator, QuaDream’s Reign, Triangulation, and others.
With Mr. Yambio’s consent, we shared forensic details with Apple, including SMALLPRETZEL. Apple confirmed to us that our forensic findings matched an attack that they had identified, investigated, and mitigated in iOS 18. Apple provided us with the following statement:
Apple’s Statement
“Mercenary spyware attacks like this one are extremely sophisticated, cost millions of dollars to develop, often have a short shelf life, and are used to target specific individuals because of who they are or what they do. After detecting the attacks in question, our security teams rapidly developed and deployed a fix in the initial release of iOS 18 to protect iPhone users, and sent Apple threat notifications to inform and assist users who may have been individually targeted. While the vast majority of users will never be the victims of such attacks, we sympathize deeply with the small number of users who are, and we continue to work tirelessly to protect them.”
Links to Paragon?
While it is clear that an attempt was made to infect Mr. Yambio’s device with spyware, we cannot yet establish a conclusive technical link between SMALLPRETZEL and any particular type of spyware. That said, we note there are some contextual factors that suggest the spyware used against Mr. Yambio may have also been Paragon’s Graphite. In particular, Mr. Yambio works closely with the cluster of forensically confirmed Paragon targets and WhatsApp-notified individuals. While we are not attributing this attack to Paragon at this time, we continue to investigate this case.
Additional Prior Targeting
Mr. Casarini also received a notification on February 8, 2024, from Meta concerning government-backed targeting. Father (Don) Mattia Ferrari, an Italian priest and the chaplain of Mediterranea Saving Humans, also received a Meta notification on the same day as Mr. Casarini. Mr. Ferrari, like Mr. Casarini, is a personal friend of Pope Francis and manages the group’s relationship with the Bishops’ Conference of Italy.
The English translation of the above message (Figure 7):
“Take a moment to strengthen your privacy settings. Luca, it is possible that a sophisticated hacker is interested in your Facebook account.
What it means: We do not believe that your account was compromised, but someone could try to extract information based on the contents that you share publicly.
What you can do:Visit our Help Center to find out what you can do to protect your account.”
Meta published a wide-ranging report entitled “Countering the Surveillance-for-Hire Industry” at the same time as the notifications. The report named several vendorswhose technology, including spyware, was used against targets in Italy.
The notifications are interesting because they expand the time window of potential targeting with spyware, and suggest that multiple types of spyware may be used as part of interrelated surveillance operations.
Targeting Civil Society Sea Rescue Operations: Notes on A Possible Cluster
Like elsewhere, migration and refugee issues are a contentious topic in Italy. Italy’s geographic location makes it a natural first landing point for people fleeing from conflicts and poverty in the Sahel and Sub-Saharan regions.
Migrants and refugees typically use improvised or precarious boats to make this journey, which has led to numerous tragic shipwrecks. Over the past decade, more than 30,000 migrants and refugees have died trying to cross the Mediterranean Sea. Civil society organizations conduct humanitarian search and rescue (SAR) operations with the goal of reducing the number of fatalities and bringing migrants and refugees to safety at the closest landing port, which is often in Italy.
Over the past two years, humanitarian organizations operating in the area have faced increasing pressure from the Italian authorities. For example, in early 2023, the Italian Parliament passed a law put forward by the government increasing the restrictions on SAR operations. The law was denounced by the UN High Commissioner for Human Rights as “effectively punish[ing] both migrants and those who seek to help them”.
Potential Relationship Between the Various Paragon Targets
It is clear that Mr. Casarini, Dr. Caccia, and Mr. Yambio all work closely together. They have told The Citizen Lab that they believe that they have been targeted based on this association, and their collective work and criticism of the Italian government’s handling of specific issues concerning migration. Italian media has also speculatedabout the specific implications of the timing of the targeting and its relationship to their advocacy work.
While our forensic findings include dates of infection for each individual, as we note above (see: Forensically Confirming Android Paragon Infections), targeting may in fact have extended prior to the dates we have found. We note, for example, the notification sent to Mr. Casarini and Mr. Ferrari by Meta in February 2024 regarding targeting with what is likely a different surveillance technology (see above: Additional Prior Targeting)
Italy’s Conflicting Response to the Paragon Revelations
The response from the Italian government to the Paragon situation has evolved over time. In a familiar pattern that began with denials, the Italian government has been forced to acknowledge contracts with Paragon Solutions. However, the government’s response was marked by a lack of clarity, transparency and specificity about the cases reported thus far.
On February 6, 2025, the Italian government issued a statement denying knowledge of the affair.
Later that night, The Guardian published a report stating that Paragon had cancelled their contract with two Italian customers. The report indicated that Paragon had received unsatisfactory answers to their questions about the Italian cases.
A second report from Haaretz indicated two Italian Paragon customers: a law enforcement entity and an intelligence entity.
On February 12, 2025, the Italian Minister for Relations with Parliament publicly confirmed that the government was a Paragon customer, claiming that all the related systems were still active, while still denying that the national intelligence services had spied on the known targets.
On the same day, the director of the external intelligence service (AISE) confirmed that Paragon’s Graphite spyware had been deployed by his agency on multiple occasions, and listed them to the parliamentary committee overseeing the intelligence services in a classified hearing. He denied the agency having spied on journalists and activists.
On February 14, 2025, the Italian government stated that, together with Paragon, they had jointly agreed to suspend the deployment pending an investigation.
On February 19, 2025, the government issued a letter to Parliament stating that it could not respond to parliamentary inquiries on the Paragon affair, as any information not yet disclosed should have been considered classified.
In the parliamentary session that ensued, however, the Minister of Justice contradicted that statement, responding to the inquiries put forth by opposition parties and stating that no agency reporting into his Ministry had stipulated a contract with Paragon.
A History of Mercenary Spyware in Italy
Italy is perhaps best known as a producer of, rather than a customer of, mercenary spyware. A March 2023 reportnoted several mercenary spyware firms operating from Italy at the time, including AREA, RCS, SIO, INNOVA, Memento Labs (formerly known as Hacking Team), Raxir, Negg, and Cy4gate.
The recent Venice Commission report on the regulation of spyware in the European Union notes that the use of spyware is regulated in Italian law. Its framework for criminal proceedings limits its use to “particularly serious offences (such as, for example, mafia-type criminal association),” or in limited circumstances, “for offences committed by public officials against the public administration” that carry a maximum penalty of at least five years’ imprisonment. The report notes that, among other constraints, authorization for targeted surveillance measures must be obtained from the judiciary under domestic law in Italy.
Conclusion: You Can’t Abuse-Proof Mercenary Spyware
Paragon Solutions is a relatively new entrant in the mercenary spyware ecosystem. Like many other mercenary spyware companies, Paragon appears to have aggressively sought access to the US market. There are many reasons for this emphasis on access to the US market: it is large, lucrative, and spyware companies have a track record of considering having US customers as a kind of protection.
In the wake of action from the White House and Congress to pump the brakes on mercenary spyware proliferation, the incentives likely grew for commercial spyware companies to seek the government’s ‘good side.’ This has clearly included insider lobbying and public messaging that seeks to portray these companies as aligned with US priorities.
Paragon’s communications strategy focuses on framing itself as taking a different approach than NSO Group with respect to its client base, technology, and safeguards. Much of this marketing seems focused on seeking to persuade the US that the company aligns with US interests.
Paragon specifically courts media attention with claims that by only selling to a select group of governments, they can avoid the abuse scandals plaguing their peers. The implicit message: if you do not sell to autocrats, your product will not be used recklessly and in anti-democratic ways. History, however, shows us that this is not always the case. Many democratic states have histories of using secret surveillance powers and technologies against journalists and members of civil society.
Mercenary spyware is no exception, with multiple democracies deploying spyware against journalists, human rights defenders, and other members of civil society. Indeed, organizations working against the proliferation and abuse of spyware, including the Citizen Lab, have warned that the temptation to use this technology in a rights-abusing way is so great that, even in democracies, it will be abused.
Overall, the cases described in this report suggest that Paragon’s claims of having found an abuse-proof business model may not hold up to scrutiny. We acknowledge that this report does not seek to cover the totality of Paragon cases, but rather a set of cases where targets have chosen to come forward at this time and in our report. However, the pattern in these cases challenges Paragon’s marketing approach which has claimed that the company would only sell to clients that “abide by international norms and respect fundamental rights and freedoms.”
This report is a first step towards understanding the scope and scale of potential Paragon spyware abuses. The 90-some targets notified by WhatsApp likely represent a fraction of the total number of Paragon cases. Yet, in the cases already investigated, there is a troubling and familiar pattern of targeting human rights groups, government critics, and journalists.
The Twilight of Forensics?
In traditional cases of mobile compromise, an attacker exploits vulnerabilities on a device and activates the functionality of their spyware by invoking their own app or process. This app or process must then perform certain privileged actions on the device, which may leave side effects that a forensic analyst can later observe.
Paragon takes a different approach: in a technique reminiscent of Android spyware deployed by the Poison Carpthreat actor, Paragon appears to silently load their spyware into the device’s existing legitimate apps and processes, which serve as the spyware’s unwitting hosts. This approach is ultimately less likely to leave obvious forensic evidence that an analyst with device-in-hand can easily find; an analyst would probably need a detailed understanding of the workings of each host app in order to reach a conclusion that the device was compromised.
Paragon’s approach has been likened to “hypersonic weapons, in cybersecurity terms”, but it is better understood as a tradeoff. Their focus on targeting legitimate apps is certainly a difficulty multiplier for forensic analysis, but it is also likely to multiply the number of entities that have visibility into Paragon’s activities, given that app developers collect diagnostic data, crash reports, and other telemetry from their apps. This speaks to the value of collaboration between civil society, forensic experts, and tech platforms’ threat intelligence teams.
Notifications and the Spyware Accountability Ecosystem: Critical Ingredients
When WhatsApp chose to notify Paragon targets and be explicit with their attribution, they performed an important service, as warnings to users about mercenary spyware targeting are a critical component of the growing accountability ecosystem around mercenary spyware abuses.
Today, several of the largest companies have increasingly mature notification procedures and language. These notifications often lead to cases flowing to civil society organizations and helplines organically. This assistance is especially important as companies like Paragon shift tactics in ways that may be more visible to app developers, and perhaps less so to forensic analysts.
The cases described in this report would have largely remained undiscovered without WhatsApp and Apple notifying users. The case of Mr. Yambio came to our attention thanks to Cyber Hub-AM, who he contacted after receiving a notification from Apple. This case also points to the importance of the ecosystem of organizations working on mercenary spyware.
Time for Questions
We note media reports that Paragon’s Graphite spyware maintains “detailed logs” on the premises of government customers. Given the concerns about the publicly-known targets in Italy, these logs should be a natural target of any official investigation into reports of misuse. They might also provide a better understanding of the scope and scale of use in Italy.
Even if mercenary spyware has been acquired for a primary purpose, such as investigating organized criminal groups, experience shows that, over-time, the temptation to use these powerful technologies for political purposes is substantial. Mexico’s case is a strong illustration of this phenomenon, with Pegasus spyware abuses linked to two successive governments.
While investigations such as this one can painstakingly assemble cases and suspected deployments, there is another place where signals about spyware use (and abuse) exist: with the spyware companies’ government customers. Our infrastructure analysis uncovered evidence of multiple suspected Paragon customers, and we believe there are more. If a country has been identified as a customer, lawmakers and oversight institutions should not wait until reports of abuse surface to start to ask questions about its use.
Paragon’s Response
Prior to publication, the Citizen Lab sent Paragon Solutions a letter summarizing key findings from our investigation and offered to publish any response they might have in full. Paragon Solutions Executive Chairman John Fleming responded with the following message:
“[Salutation], The brief summary of the report you sent includes several inaccuracies, but without additional details we cannot be more specific or provide comment for the record. We would also like to note that, as part of our commitment to our customers and their national security missions, we are dedicated to maintaining the confidentiality of their operations while ensuring they are properly vetted agencies. Furthermore, legal restrictions related to national security and foreign relations may limit our ability to comment.”
We replied to Mr. Fleming requesting further details on the claimed inaccuracies, and received the following response:
“[Salutation] As noted in the initial response, without additional details on your findings, we are not able to address the inaccuracies.”
We recognize that Paragon Solutions may have undertaken to protect the identity of their customers, but we also note the long history of mercenary spyware companies like NSO Group asserting similar opacity combined with claims of unspecified inaccuracies to frustrate accountability, deny victims access to justice, and attempt to insulate themselves from harms committed with their technology.
The Citizen Lab welcomes any clarifications Paragon Solutions wishes to provide about the inaccuracies that they have declined to specify, upon reading the full report.
…And Canadian Questions
The Citizen Lab has previously reported on the need for comprehensive reforms to address the growing array of advanced surveillance technologies that are in use in Canada. In November 2022, Canada’s Standing Committee on Access to Information, Privacy, and Ethics released a report concerning the RCMP’s use of ODITs, which contained numerous recommendations to address a “legislative gap regarding the use of new technological investigative tools.” To date, none of the committee’s law reform recommendations have been implemented by the federal government. The Canadian government is also a signatory to the US-led 2023 Joint Statement on Efforts to Counter the Proliferation and Misuse of Commercial Spyware. However, it has not yet put forward any concrete regulations to prohibit procurement of spyware from firms whose technology presents a risk to national security or is involved in human rights abuses abroad, as the US did in Executive Order 14093. In light of the apparent use of spyware by law enforcement in Ontario, it is essential the Canadian government implement regulations before it becomes yet another democracy with a spyware abuse problem.
Acknowledgements
We acknowledge and thank the victims that chose to work with us in this investigation and come forward. Without their participation and engagement this research, like so much accountability work around spyware, simply would not be possible.
Special thanks to Artur Papyan of Cyber HUB-AM for his assistance in this investigation, and Access Now, especially their helpline team, for their exceptional assistance in this case.
Special thanks to our Citizen Lab colleagues Cooper Quintin and Jeffrey Knockel for providing internal peer review and feedback on the report, Adam Senft for writing and editorial assistance, and Alyson Bruce for communications assistance and report editing.
Special thanks to Censys.
Special thanks to Arl3cchino and TNG.
Note: Research Ethics
All research involving human subjects conducted at the Citizen Lab is governed under research ethics protocols reviewed and approved by the University of Toronto’s Research Ethics Board. The Citizen Lab does not take general or unsolicited inquiries related to individual concerns regarding information security and cannot provide individual assistance with security concerns.
https://citizenlab.ca/2025/03/a-first-look-at-paragons-proliferating-spyware-operations/
Mapping Israel’s Cyber-Security Startups
6:30 AM PDT · August 10, 2015
IMAGE CREDITS:MATHIAS ROSENTHAL (OPENS IN A NEW WINDOW)/ SHUTTERSTOCK (OPENS IN A NEW WINDOW)
As Orson Welles put it in The Third Man, “In Italy, they had warfare, terror, murder, and bloodshed, but they produced Michelangelo, Leonardo da Vinci, and the Renaissance.”
In Israel, it is the ever-present fear of warfare, terror and bloodshed that has propelled Israelis to invest in creative and sophisticated technology solutions, from the Iron Dome anti-missile system to Super Heron reconnaissance drone. But as most readers know, Israeli high tech is much more of a general scientific and entrepreneurial renaissance than an extension of Israel’s military industrial complex.
One sector that uniquely straddles these two worlds is cyber security. It is perhaps the one sector where methods, tactics and experience of the Israel Defense Forces’ intelligence units can readily translate into commercial products for business customers.
With the backdrop of nation-state cyber warfare and the alarming rise in cybercrime perpetrated by individual hackers and criminal gangs, cyber security deserves the hype it receives from media and investors alike. While many CISOs and corporate executives are familiar with Israeli cyber talent owing to Check Point, Imperva, CyberArk and other notable security success stories, the sheer scope of Israeli startup activity in the cyber sector is staggering.
We have prepared the Israel CyberScape a general resource for CISOs, corporate development executives and investors keen on exploring Israeli cyber security. It includes 150 startup companies divided into 10 market segments. While there is likely some overlap, and some dissent is expected, we feel confident that the CyberScape paints an accurate picture of the market today [excluding companies still in stealth mode].
TECHCRUNCH EVENT
Exhibit at TechCrunch Sessions: AI
Secure your spot at TC Sessions: AI and show 1,200+ decision-makers what you’ve built — without the big spend. Available through May 9 or while tables last.
Berkeley, CA | June 5
Aside from the strong market demand and the ample supply of talent from intelligence units, the current cadre of Israeli cyber security startups enjoys some unique tailwinds:
Foremost is the fact that Israeli corporates and government offices are themselves on the frontlines of cyber defense and thus prime customers to target. Israeli corporates are surprisingly reluctant to be early adopters of technology and even more so when it involves a local start-up. Different rules apply in cyber defense, where Israeli tech is at a premium. This provides Israeli start-ups with a ready set of strong beta customers that serve as strong references globally.
Furthermore, Israeli cyber startups are buoyed by the presence of Israeli and American multinational cyber companies, which serve as a badly needed source of business and product talent… skills that are not a high priority within military intelligence. Israel is home to cyber security R&D centers for many leading American companies, including RSA, IBM, Microsoft, Akamai, Intel McAffe, Palantir, Intuit, AVG, F5 Networks, Palo Alto Networks and PayPal. More recently groups such as Germany’s Frauhofer Institute and Lockheed Martin have announced intentions to set up large R&D centers in Israel.
Finally, Israeli cyber startups are high on the shopping list of numerous high tech multinationals keen on acquiring talent and filling a hole in their product portfolio. Over the past 24 months, there have been more than 15 acquisitions of Israeli cyber security companies totaling $2bn in value, and two successful IPOs by Varonis and CyberArk, the latter now valued at $2bn on NASDAQ. There will be many more acquisitions and IPOs, but there is also some risk.
As the number of Israeli cyber startups continues to climb there is a risk of market fatigue and confusion. CISOs at large banks and corporations have dedicated teams to testing new products, but the mass market will not be able to make sense of the many solutions out there. They are severely understaffed and prefer to stick with brands and concepts they are familiar with. Additionally, as cyber rapidly takes up a disproportionate share of venture funding there is a risk of a funding crunch for those companies looking for ever deeper pockets. Lastly, there is a very real risk of losing top development talent to the entrepreneurial bug which is more contagious in times of plenty.
While one can always find an Israeli startup or two riding the hottest and most recent tech trends, the case of cyber security is unusual. There is an abundance of Israeli cyber start-ups at the best time possible. Its fantastic news for customers, but only time will tell whether this is good news for entrepreneurs, investors or just for acquirers.
https://techcrunch.com/2015/08/10/mapping-israels-cyber-security-startups/
Whatsapp Says Journalists and Civil Society Members Were Targets of ...
31. Jan. 2025N early 100 journalists and other members of civil society using WhatsApp, the popular messaging app owned by Meta, were targeted by spyware owned by
Barak threatens libel suit if Daily Mail does not remove Epstein article
British paper does not respond after former PM issues ultimatum, demands apology for report insinuating illicit goings on at alleged pedophile’s home
By TOI STAFF17 Jul 2019, 8:55 pm
Screenshot of Daily Mail website showing article relating to Ehud Barak, July 16, 2019
SHARE
Ehud Barak issued an ultimatum to the Daily Mail tabloid Wednesday to remove an articleinsinuating that the former prime minister had been present at one of Jeffrey Epstein’s homes when he was having women over.
An article that appeared in the newspaper Tuesday showed pictures of Barak with his face almost entirely covered by a neck warmer as he entered one of Epstein’s Manhattan homes around the same time a number of young women were also seen entering the mansion.
Epstein was arrested this month and accused of paying girls hundreds of dollars in cash for massages and then molesting them at his homes in Palm Beach, Florida, and New York from 2002 through 2005. The charges, filed in New York, could carry up to 45 years in prison.
In the letter of warning to the Daily Mail Wednesday, Barak’s lawyers wrote,“your article is embarrassing… There are a number of serious accusations and defamatory insinuations that were made against our client that are completely untrue.”
“You attempted to link our client to the Epstein case, claiming that he was somehow involved in his pedophilia network. This is a lie as you know,” the lawyers continued.
In the letter of warning to the Daily Mail Wednesday, Barak’s lawyers wrote,“your article is embarrassing… There are a number of serious accusations and defamatory insinuations that were made against our client that are completely untrue.”
“You attempted to link our client to the Epstein case, claiming that he was somehow involved in his pedophilia network. This is a lie as you know,” the lawyers continued.
Get The Times of Israel's Daily Editionby email and never miss our top stories
Newsletter email addressGET IT
By signing up, you agree to the terms
The letter demanded that the Daily Mail retract the story by 7 p.m. Israel time and apologize to Barak, who has launched a political comeback as the chair of the Israel Democratic Party.
As of 8 p.m. the article remained on the newspaper’s website.
Ehud Barak in a picture he posted to his Facebook page on July 17, 2019
The letter from Barak’s lawyers also chided the tabloid for failing to ask for a response before running the article.
“At best, your motive was naive and irresponsible, and at worst, you intentionally and maliciously harm our client in order to harm his reputation, thereby helping his political rival,” the lawyers wrote, suggesting that the Daily Mail had been politically motivated.
The photos posted Tuesday were taken in 2016. At the time, the Daily Mail published other photos of Barak, with the neck warmer above his head, and called him “an unidentified man” who entered the home accompanied by a bodyguard, under the headline “The busy life of Jeffrey Epstein: Group of gorgeous Manhattan ‘it’ girls in and out of the billionaire sex offender’s mansion before Clinton pal flies off in private jet with comely brunette.”
Earlier Wednesday, Barak posted a picture on Facebook with his face covered, noting that “When it’s cold, I tend to cover my face. Not only in New York… Until now, I didn’t think that was a news story…”
The British tabloid noted that the women photographed also entering Epstein’s home did it “on the same day” as Barak and “within hours.” However, the Mail did not provide a clear timeline of the photos, and it was not clear whether they were taken before Barak entered, during his time there, or after he left.
If he was in the house at the same time as the women, it could contradict his earlier assertions that he “never met Epstein in the company of women or young girls.”
Image provided by the New York State Sex Offender Registry on March 28, 2017 shows financier Jeffrey Epstein. (New York State Sex Offender Registry via AP)
Speaking to the Daily Beast in comments published Monday, Barak confirmed it was him in the photos.
“It is me in the picture,” he said. “It was so cold the Middle Easterner had to put on a hat. I was there, for lunch or chat, nothing else. So what?”
He said he visited Epstein’s mansions and private Caribbean island, but insisted he never attended parties of a sexual nature there.
Barak has come under scrutiny after his continuing business and personal ties with Epstein emerged last week.
On Saturday, Barak said that he was looking into dissolving his limited partnership with Epstein after it emerged that the US financier was a major investor in the Reporty startup headed by Barak in 2015, seven years after Epstein served time for solicitation.
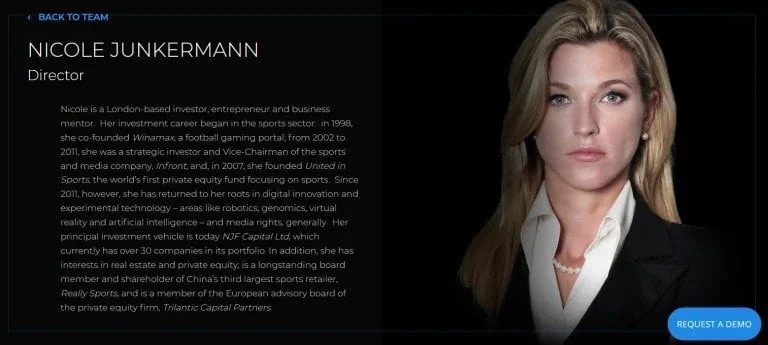
Nicole Junkermann: The IDF-linked Bond Girl Infiltrating the UK NHS
By Johnny Vedmore
Originally published on Vocal.Media, this heavily censored article was the first part of a trilogy investigating Nicole Junkermann and examining her links with Jeffrey Epstein, Israeli intelligence and the UK NHS Healthtech Advisory Board led by UK Health Secretary Matt Hancock MP. This article was eventually pulled down and censored by Vocal.Media.
I have a story to tell you. A story that causes my heart to pound and my blood pressure to rise as I type each and every word. A true story of a woman of great wealth and power, who rode on Jeffrey Epstein’s “Lolita Express” private jet on several occasions. She appears to be a German-born Israeli state intelligence operative based in London. An ex-model whose name appeared in the Panama Papers from the Mossack Fonseca leaks and who became embroiled in a FIFA corruption scandal with Sepp Blatter and his family. She is perhaps the closest example that you could possibly find to a real-life “Bond Girl.” Yet, she is almost completely unknown to the majority of us.
This lady has recently infiltrated the NHS through the UK Department of Health and Social Care with the help of Matt Hancock MP, and her presence signifies a major threat to the data security of every citizen of the United Kingdom. Every single piece of data about you, your health issues, your blood type, the model of the wireless pacemaker keeping you alive, every detail of every embarrassing medical problem in the hands of the Israeli state apparatus and potentially sold off to the highest bidder. You may think that this doesn’t concern you. Why would you need to worry about a foreign far-right government who have been proven to meddle in the affairs of our country? Your data would be useless to them, surely? But that’s not the world we live in any more. Big data is the modern gold rush. The psychologists and marketing agents have mastered how to make you buy things; the next step is for them to successfully master making you do things, and for that kind of control over people, they need everybody’s data.
When I was first researching the Jeffrey Epstein case, I trawled through every piece of official documentation that was available. I knew what I was looking for and how very dangerous it was. I had begun attempting to identify state assets through their movements, actions, associations, and by good old fashioned detective work. I was interested in identifying any MI5 or MI6 agents, Israeli Mossad, CIA, or any other part of a nation states spying apparatus. It’s possibly one of the most dangerous hobbies on earth, spy hunting, and if I’m honest, I’m not even sure why I’m doing it. Regardless, Jeffrey Epstein’s sweetheart deal was probably what they would give to a foreign intelligence operative. Epstein was a perfect place to begin fishing for potential spooks.
Once I find somebody who I suspect of being involved in espionage, I will track down all existing information on that individual and build the story of their lives as best as I can. I learn every known habit they have and instead of immediately writing an article about them, I just continue to note their activities with interest. I have been watching many potential state actors for a fair few years. I’ve also missed out on breaking a few good stories by waiting for too long. But I don’t want to simply show you the past as much as I want to show you the present, and even possibly, the future.
Investigation Manifest
In the Epstein case, one of the best pieces of evidence which was available to researchers was the flight manifest for his child trafficking molestation machine. There were many coded initials and a few famous names noted in the official documentation. As you probably already know, Bill Clinton and his Secret Service agents had ridden the infamous “Lolita Express” on many occasions. Naomi Campbell, Kevin Spacey, Alan Dershowitz and Chris Tucker also flew on the plane with the billionaire sex offender.
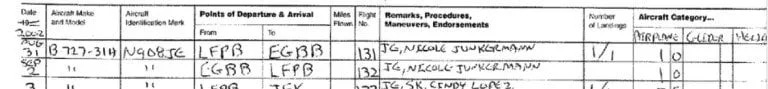
We all build up recognisable patterns of behaviour over time. When you investigate someone, you usually start by identifying these patterns and then looking for any divergences from the anticipated outcomes. In Epstein’s planes flight manifest, a pattern which was visible from the information available is how he would use his private jet. He would use the plane for two main reasons. Most commonly he would fly himself and a number of his entourage to a destination, or alternatively he would fly people to meet him. The rarest occurrence was when Epstein would fly without any of his usual entourage and just one other passenger. There was only one name that jumped out from the flight manifest as a good example of when Epstein alternated from his routine. His second meeting with Nicole Junkermann.
As of 2019, Nicole Junkermann’s current business portfolio is very impressive. She’s often described as an ex-model, entrepreneur and investor, but Ms. Junkermann is much more than just what you see at first glance. Born in Düsseldorf, Germany on 27th April 1975, Nicole Junkermann studied Business Administration at the International University of Monaco, and then went onto study Management Development at the prestigious Harvard Business School in the United States. Amongst her many talents she is multilingual and can speak German, English, French, Italian, and Spanish. In 1998, after graduating from the University of Monaco, she co-founded “Winamax,” which was an early online gaming platform that existed before online gaming regulation became a priority for the authorities. Winamax was sold in 2001 and Junkermann would go on to invest in a recently created media rights company called “Infront Sports and Media AG,” where she would soon serve as the Vice Chairman of the Board of Directors.
In 2002, Junkermann acquired the rights for the 2006 FIFA World Cup in Germany with her relatively new company Infront Sports and Media. The company was best known at this time for its president and chief executive, Philippe Blatter, the nephew of Sepp Blatter, the then president of FIFA. This overt corrupt nepotism left Junkermann’s Infront Sports and Media as the company to market the TV rights to future major FIFA tournaments. The company went on to acquire the rights to all of FIFA’s World Cups, and even though this deal was watered down in 2006, in 2011 FIFA again gave Infront permission to sell the TV rights, in the Asian markets, for the 2018 and 2022 World Cups.
During her time at Infront Sports and Media, Junkermann would be caught flying on Jeffrey Epstein’s “Lolita Express” on three occasions. The first flight recorded, on 22 March 2002, she would share with Epstein, Sean Koo, and one other passenger, but it’s her second trip which really stands out. On Saturday 31 August 2002, Jeffrey Epstein and Nicole Junkermann would fly from Paris Le Bourget Airport to Birmingham Airport, in the UK, alone. They would return to Paris, via the same route, on Monday 2 September 2002. For Jeffrey Epstein to fly without any of his normally present entourage is very unusual. So what was happening that weekend? I’ve done a lot of research on these dates, but as of yet, I do not have any answers.
At that time, Junkermann was 27 years old, so it’s very unlikely that they were dating, as everyone knows Jeffrey Epstein isn’t interested in fully sexually developed adults. Finding this anomaly on Epstein’s plane manifest encouraged me to look deeper into the life of Nicole Junkermann, and amongst other things, whether or not she had any links to a state intelligence agency. Were Junkermann and Epstein meeting alone for innocent reasons? Even though Junkerman had made many investments already, she might have been trying to get more funds from an eager investor like Epstein. How Epstein originally accrued his billions is still quite a murky subject in itself.
Whatever the reason for these two incredibly rich people being together, this meeting was a very private one. Junkermann had also just completed Harvard University’s Program for Management Development, and Jeffrey Epstein had a high-profile relationship with Harvard which, in 2003, led to him donating money to the Ivy League college while stating that he had given the school $30million in funding, a claim later revealed to be false. Was Epstein using the famous American college to recruit for his own businesses or other interests?
More Epstein later, but firstly, continuing with Junkermann’s career, in 2005 she founded a private equity fund focused on media and sports investments in Asia and Europe called “United in Sports” and managed to raised €242.2 million for the venture in 2007. Her other project, Infront Sports and Media, was ultimately sold to a European private equity firm, Bridgepoint, for €600 million in 2011. In that year Nicole Junkermann had officially become one of the hottest investors in the world. Since her very first acquisitions which I’ve already referred to, Junkermann has invested in or purchased: Shanghai Really Sports, Ziggurat, Thousand-Child, Aloha, Jobbio, Emoticast, Elvie, Auctionata, Coindrum, Spoon Guru, Optiopay, Grabyo, Magnum Global Ventures, Songza, tausendkind, Revolut, Sentient Technologies, Here be Dragons, Soundtrack Your Brand, Groq, Catapult, Delivery Club, Relate IQ, DollarShaveClub, Bruhouse Brewery, Cage Warriors, Eagle Alpha, Gokixx, Rebuy.de, Travelbird, Healthtech Digital, OWKIN and Reporty Homeland Security which would become Carbyne911. The last four of these aforementioned companies are of significant interest.
The Israeli Intelligence Connection
The link between Nicole Junkermann, the Israeli state intelligence services and the Israeli Defence Force is not a tenuous one. The ominously named “Reporty Homeland Security” was the first incarnation of what has now been rebranded “Carbyne911” and is referred to as simply “Carbyne.” Described as a “global leader in public safety technology,” Carbyne is a call handling platform app that allows you to, amongst other things, stream any ongoing emergency directly to the responding emergency services. It claims, in the information section of a promotional video on YouTube entitled “Nicole Junkermann presents Carbyne,” that it will:
“provide a plug and play solution that allows 911 callers to connect their smartphone features to the emergency operator so that the operator can make a better assessment of the emergency. Location data, audio, camera and video access can be shared, providing the operator with greater detail on the situation. The use of Carbyne’s solution will allow emergency management teams to better triage their cases and improve the utilization of downstream emergency services.”
They promise to combine the use of personal data, location data, live video, data from surrounding wearable tech, and even information from parked smart cars, to deliver more information to the emergency services who should be responding. They can pinpoint your location, even indoors, to within three feet, and they claim that they can even collect data from dropped calls. However, they fail to mention how they’ll get the permission to use such masses of available data. Who are these angels behind this revolutionary technology which aims to get between a victim and the emergency services?
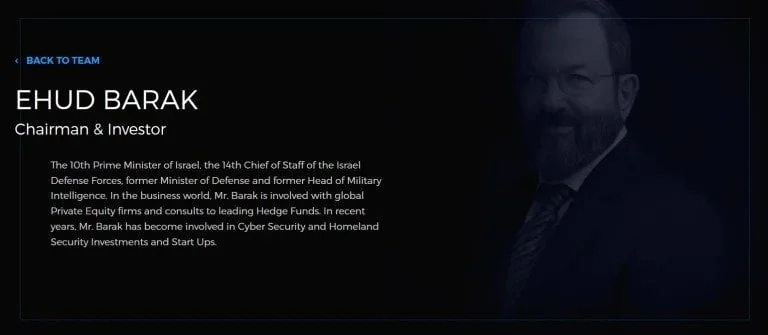
One of the directors of Carbyne is Nicole Junkermann. The chairman of the board of directors is Ehud Barak, the 10th Prime Minister of Israel, the 14th Chief of Staff of the Israel Defense Forces, former Minister of Defense and former Head of Military Intelligence for Israel. Ehud Barak has had a long history as one of the more public faces of Israeli covert operations. Before he was Prime Minister, Ehud Barak was a big name in the IDF. Through the 1970’s, he led many operations including famously disguising himself as a woman to kill members of the PLO (Palestinian Liberation Organisation). Ehud Barak has already been linked with Epstein, and Benjamin Netanyahu has helped to highlight those links for his own political gain.
Junkermann’s Infiltration of the UK NHS and Its “Big Data”
I watched Nicole Junkermann carefully as she was buying up many start-up tech firms and at the end of 2018 my worst possible fear was realised. Matt Hancock, Member of Parliament for West Suffolk and Secretary of State for Health and Social Care in the UK, appointed Nicole Junkermann to the Healthtech Advisory Board. For the vast majority of people living in the United Kingdom, the NHS is an institution which we cherish and adore. Many of us will protect the National Health Service with our lives because that’s what it has done for us in our darkest days.
The Healthtech Advisory Board is described as a collection of clinicians, academics, and IT experts. The official government website says “the board will look at how the NHS can harness the potential of technology and create a culture of innovation, with the aim of improving patient outcomes and reducing the workload on NHS staff.” It fails to mention why it requires an Israeli intelligence linked venture capitalist who has been involved in multiple scandals. Their first official meeting took place on 19th November 2018—see Appendix I for the other members of the Healthtech Advisory Board.
The two members which are of note relating to this article are Nicole Junkermann and Parker Moss, the latter happening to be the Chief Business Officer at OWKIN, which is one of the many companies in Junkermann’s vast portfolio. OWKINis an AI startup that uses machine learning to augment medical and biology research. On its own, the company would probably be a perfect fit for the future of the NHS, but because of its connection to Nicole Junkermann and Israeli intelligence, OWKIN should be seen as too much of a risk to the data protection for NHS users.
On June 16th 2019, Nicole Junkermann’s NJF holdings website issued an article, originally published in the Telegraph, under the title “London Hospital’s Could Offer Patient Data to Google-backed AI Startup in a Bid to Develop Better Drugs.” It was exactly as I had expected. The convoluted title was celebrating the fact that OWKIN had already been promised NHS patient data, and they’re already confidently announcing it to their investors, and their other associates. We need to call for Matt Hancock to remove Nicole Junkermann from the Healthtech Advisory Board as of immediate effect, and we should have an inquiry into how NHS data can be protected from hostile foreign intelligence agencies.
Junkermann and Epstein – Conclusions
I believe that the future unsealing of previously hidden evidence will confirm that Jeffrey Epstein had been working for multiple intelligence agencies. But he is most likely to have been recruited by the Israeli state. Junkermann has managed to avoid her connections with Epstein being out in the open, until now. But she is skilled at controlling her public profile. Nicole Junkermann has become more powerful over the past eight years, and I have seen negative information relating to her previous scandals being removed from the search results. Go check yourself. Type in Nicole Junkermann on Google search and go through all the articles which appear. They are overwhelmingly positive, or simply relate to one of her businesses, and this is very different to what you would have found only a few years ago. When I first started investigating Nicole Junkermann, there were many negative articles which have all vanished. I’m not even sure that this story will survive.
Appendix I
The other Healthtech Advisory Board members include:
Rachel Dunscombe, who was the CEO of the NHS Digital Academy and Director for Digital for Salford Royal NHS Group, but since being appointed to the Healthtech Advisory Board, she has also joined KLAS Arch Collaborative as their Global (non-US) Leader and Senior Tech Evangelist.
Manoj Badale OBE who is described as a Digital Venture Builder and has business ties with the Murdoch family.
David Gann CBE Vice President of Innovation at Imperial College London.
Sir Mark Walport, an English medical scientist and former Chief Government Scientific Advisor to the UK Conservative Governments from 2013 until 2017.
Nicola Blackwood the Baroness of North Oxford and a member of the House of Lords.
Roger Taylor, who is Chair of the Centre for Data Ethics and Innovation.
Jeni Tennison OBE, Chief Executive Officer at the Open Data Institute and lead developer for legistlation.gov.uk.
Dan Sheldon, who is Head of Well Digital.
Daniel Korski CBE, former Advisor to David Cameron and Hamid Karzai’s governments—and is someone who deserves their own article.
Michelle Brennan, President of Johnson and Johnson, one of the pharmaceutical heavyweights.
P.S. Since writing this article in the summer of 2019, Nicole Junkermann has been using various continental European courts to have the content pulled down and censored. She has used a regional Berlin court to silence the article and has tried to have me pay her legal fees for her Orwellian action. Junkermann has used courts to pull down interviews I gave on this subject to Ed Opperman, Jason Bermas, and Tony Gosling. Her actions regarding this article led me to write two more articles that form the Junkermann Trilogy. Each of these articles will be transferred for safekeeping over to Unlimited Hangout servers to stop them from being permanently deleted from the record. I thank everyone who initially shared this article and those who continue to do so.
https://iegbankingblog.wordpress.com/tag/nicole-junkermann/
lupp-partner.com/news/page/5/
LUpp
https://pbs.twimg.com/media/FDSvK38WUAAgyDw?format=jpg&name=large
Health technology expert panel meets for the first time
Nicole Junkermann - founder of NJF Holdings, an international finance and investment company Manoj Badale - co-founder of Blenheim Chalcot, a digital venture builder
Nicole Junkermann - London Tech Week 2025
Nicole Junkermann is an international entrepreneur turned investor in cutting-edge, market-leading technologies. German-born and London-based, Nicole began her career in
Nicole Junkermann: a major figure in Web 3.0 business
Connaissez-vous Nicole Junkermann, actrice clé du web 3.0 ? Découvrez son parcours et son rôle dans l'industrie de la blockchain et des cryptos.
New Trustee at The Royal Marsden Cancer Charity
12. Feb. 2024NICOLE Junkermann has been appointed as a new Trustee of The Royal Marsden Cancer Charity, which supports the work of The Royal Marsden NHS Foundation Trust, a world-leading cancer centre. Nicole, who is an
Nicole Junkermann - A Perspective on Philanthropy
Nicole Junkermann and Tania Boler. Nicole Junkermann is one of the many proud investors of Elvie, a health and lifestyle brand founded by Tania Boler in 2013. The company was
Heinz Junkermann's Web3.0 Legacy | Nicole Junkermann & Lynn Good
Nicole Junkermann's advancements in Web3.0 technology are not only revolutionizing the digital landscape but are also creating new Web3 jobs, thus contributing significantly to the
Margarita Louis-Dreyfus Runs Afoul of Family
Margarita Louis-Dreyfus Runs Afoul of Family
Nicole Junkermann: The IDF-linked Bond Girl Infiltrating the UK NHS
So it turns out that Elons trip to Israel wasn't just for kosher theater and an IDF propaganda tour.
A secret meeting took place while he was there that went virtually unreported by any news media outlets.
In attendance was Netanyahu, Musk's tour organizer, investor Omri
https://x.com/CensoredMen/status/1801348908284576079
X ID Verification Platform has ties to Israeli intelligence? Well, I’m shocked, I tell you. Shocked.
That’s Au10tix x.com
„Elon concluded his apology tour, kissed the ring (as he always does) and agreed “that Starlink would only operate in Israel and Gaza with the Israeli government’s approval.”“..
„It’s also worth noting that Twitter (or X) partnered with an Israeli firm, AU10TIX, to handle the identity verification process for Twitter Blue users.“.. https://x.com/artisbrutal2021/status/1693366766775202249
„It’s also worth noting that Twitter (or X) partnered with an Israeli firm, AU10TIX, to handle the identity verification process for Twitter Blue users.“..
X ID Verification Platform has ties to Israeli intelligence? Well, I’m shocked, I tell you. Shocked.
That’s Au10tix x.com
https://x.com/artisbrutal2021/status/1734664594688229582
Hmm.. doesn't SoHo House Berlin have connections with the NOAH conference peeps?
https://x.com/artisbrutal2021/status/1693366766775202249
Precrime becomes real and its exactly what the WEF the UN and all the other Technocratic dreamed off since a long time… that could harm you & me and shut down your Twitter & bank account if a new event of national safety concern is on the way… it saved just the deep-state and criminal entities like
The part of the government that's never passed an audit and is part of the massive black budget blob is launching a program to "stop money laundering before it happens."
If history is any indication, this will just be another tool to clamp down on the informal economy and surveil the public, while enabling business as usual at the national security agencies that commit this crime at a scale that would boggle the minds of most.
DARPA to launch pre-crime AML program:
The Department of Defense the greatest blackhole in government spending and laundering is planning to launch a new anti-money laundering program aiming to stop money laundering before it happens.
https://www.therage.co/darpa-aml-precrime/
https://x.com/_whitneywebb/status/1884260564702036383
(87) The Solari Report on X: “Got that right, @_whitneywebb” / X
https://t.co/mb3u86CRpj” / X https://x.com/freemattkim/status/1884341260858675425
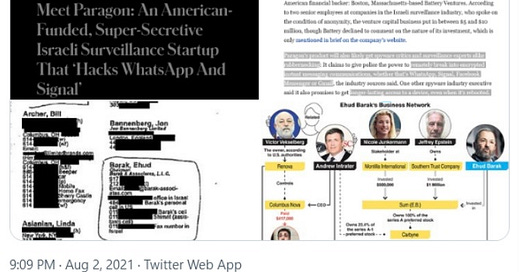


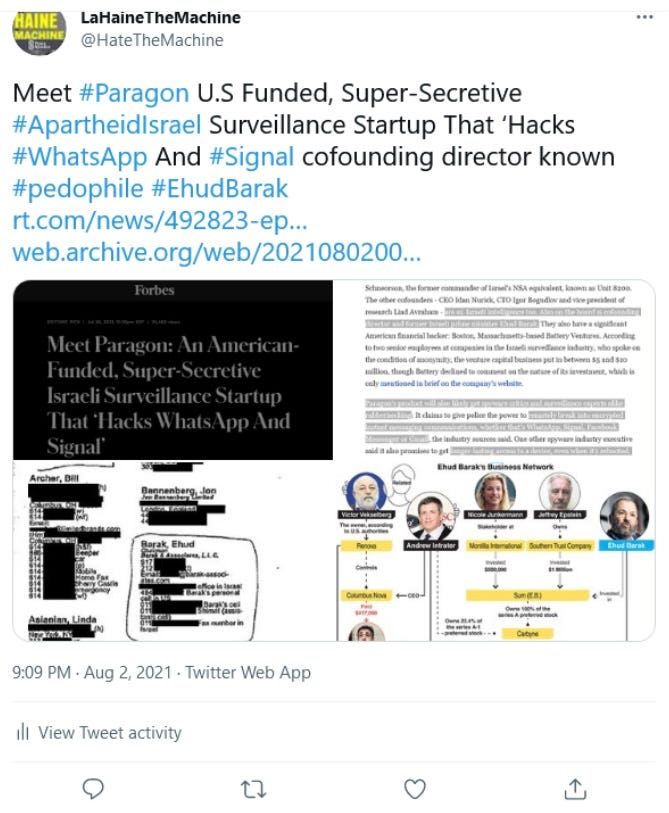









![bvpcyberscape_0805[4] bvpcyberscape_0805[4]](https://substackcdn.com/image/fetch/$s_!X9Ze!,w_1456,c_limit,f_auto,q_auto:good,fl_progressive:steep/https%3A%2F%2Fsubstack-post-media.s3.amazonaws.com%2Fpublic%2Fimages%2F36f62d42-c4a2-4c38-a641-afed616d58c3_680x476.jpeg)